After the iCloud incident there was an increased call by some information security professionals to online services providers to make two-step (or two-factor) authentication a default for all accounts. The argument is that the simple username and password combination is too weak to protect publicy accessible Internet services.
I have two-factor (and two-step) authentication enabled on a number of Internet accessible accounts including iCloud, WordPress, Facebook, LinkedIn, etc. I created randomly generated complex passwords that are unique to each account. I store these passwords in a password vault1 on my phone and on my computer because they are too complex to remember. It is impossible for me to login to my online accounts without first looking my username and password (the first factor) up in the password vault and then entering a randomly generated PIN (the second factor). It’s inconvenient but I feel a certain level of assurance that my accounts won’t be compromised by a brute force attack.
While I agree that two-factor provides an increased level of security, it does present some challenges for the average consumer. This screen shot is an example of where two-factor becomes a hurdle.
[fusion_builder_container hundred_percent="yes" overflow="visible"][fusion_builder_row][fusion_builder_column type="1_1" background_position="left top" background_color="" border_size="" border_color="" border_style="solid" spacing="yes" background_image="" background_repeat="no-repeat" padding="" margin_top="0px" margin_bottom="0px" class="" id="" animation_type="" animation_speed="0.3" animation_direction="left" hide_on_mobile="no" center_content="no" min_height="none"]
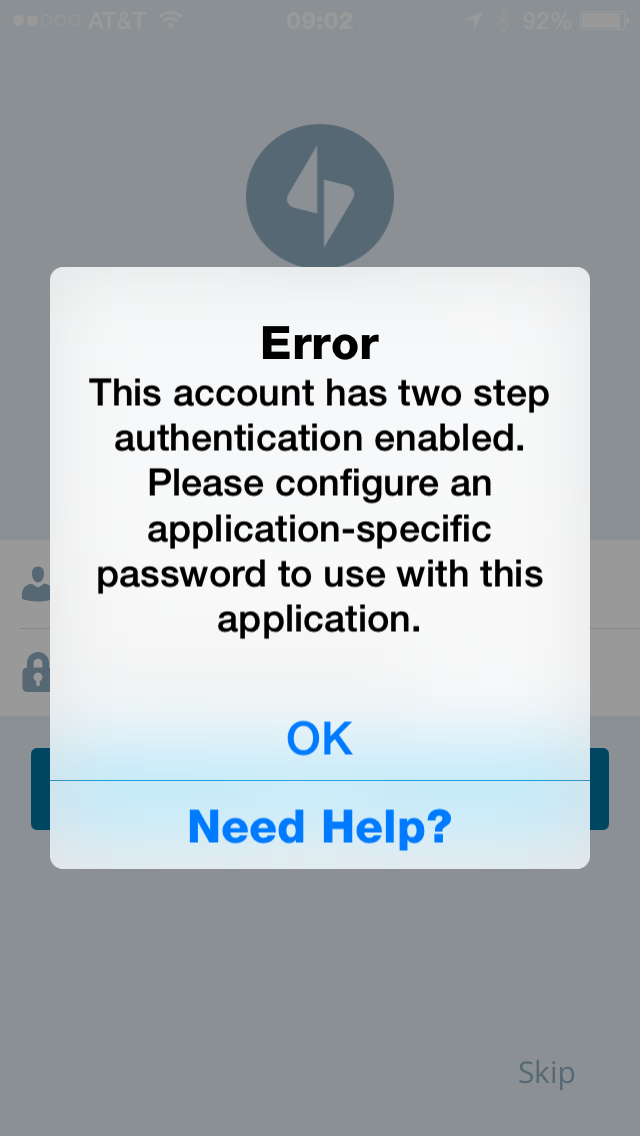
Some applications are two-factor aware and offer a way for the user to enter the two-factor PIN. But most — email, calendar, etc. — are not. Some services understand that users may encounter this problem once two-factor is enabled. Google, Apple, etc. offer a work around in the form of application specific passwords.
For example, for Google services, I can create a randomly generate password that I can enter into the password field for my mail app on my computer. I only get to use the application password once. It can not be reused. Once my application has been registered to Google I can access my account via that application on that specific device. I need to create a new application specific password for each application that connects to the service on each device.
One for email on iPhone. One for email on my iPad. One for email on my MacBook. One for email on my iMac.
Now do the same for calendar. And contacts. Keep going.
Consumers are not going to do this. The average consumer probably gave up after the second application specific password. And then turned off two-factor.
Until applications developers update there apps to support two-step authentication, consumer will continue to ignore this security feature. Convenience wins.
- I use 1Password to create 12-18 character complex passwords and a strong easy to remember password to unlock the vault. ↩
[/fusion_builder_column][/fusion_builder_row][/fusion_builder_container]

Comments are closed.