I created a Ubuntu Server to host a few security-related tools for experimentation and learning. But after installing the firewall I was stuck. I had a very difficult time trying to get the OpenVAS security scanner up and running on Ubuntu 10.04. After many failed attempts I discovered that Ubuntu 10.04 was not my best choice for a host. Ubuntu 10.04 is an older version of the distribution. Most of the security tools I want to use are deprecated on that version. I want to use the newer version of the security tools. So I installed OpenVAS and upgraded to Ubuntu 14.04.2 LTS via the do-release-upgrade command.
After upgrading to the latest release of the Ubuntu I re-installed OpenVAS. But ... I ran into other issues. The OpenVAS client requires X Windows. I had intended running Ubuntu as a headless server so this was disappointing. I did not and do want to install an X client on the server. I have the XQuartz X Windows server software on the iMac so I tried using that to server the display. It didn't work at all.
root@ubuntuserver: export DISPLAY:10.0.1.7:0.0
root@ubuntuserver:~# openvas-client localhost 88
(openvas-client:10152): Gtk-WARNING **: cannot open display: 10.0.1.7:0.0
Aargh! I'm not sure what I'm doing wrong. Perhaps I have ports blocked on my Mac. I spent a few another 30 minutes in a futile attempt to get this work before calling it quits on OpenVAS.
After thinking for a bit and doing some web searching I discovered that Tenable offers a Nessus Home edition of Nessus that I could install on my Ubuntu server. The Nessus Home edition is for private non-commercial use. With Nessus® Home I can scan my personal home network with some limitation. Each scanner will be limited to 16 IP addresses. I have almost 20 devices on my network but at least 8 of those are iOS devices. I'm not sure of the utility of scanning those. Apple doesn't provide any tools for blocking ports, so scanning them is moot.
I used Lynx to download the package to my server and I installed the package and started the daemon.
root@ubuntuserver:~# dpkg -i Nessus-6.3.4-ubuntu1110_amd64.deb
root@ubuntuserver:~# service nessusd start
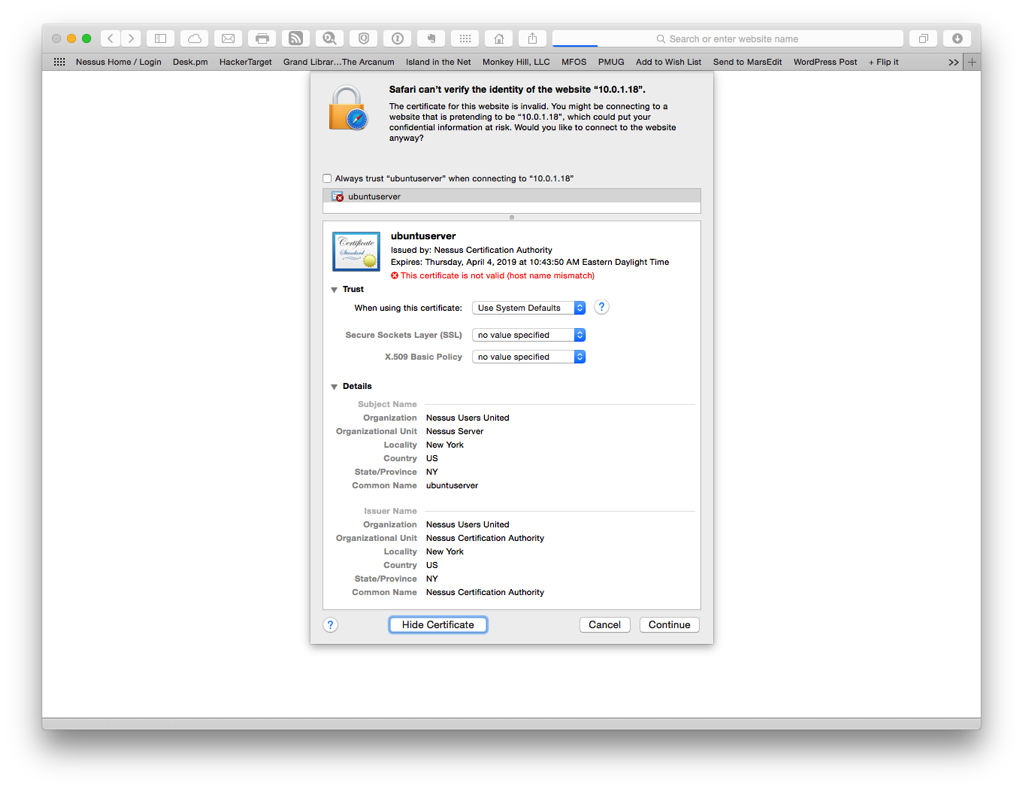
Before I could complete the setup I made sure to register for an activation code. Once I received my activation code, I opened Safari and entered the following URL: https://10.0.1.18:8834/. The Nessus server is pre-configured to use a self-signed SSL certificate.
Once I accepted the certificate I created a user account and registered my installation with Nessus. The registration is important if you want to receive updated scan signatures.
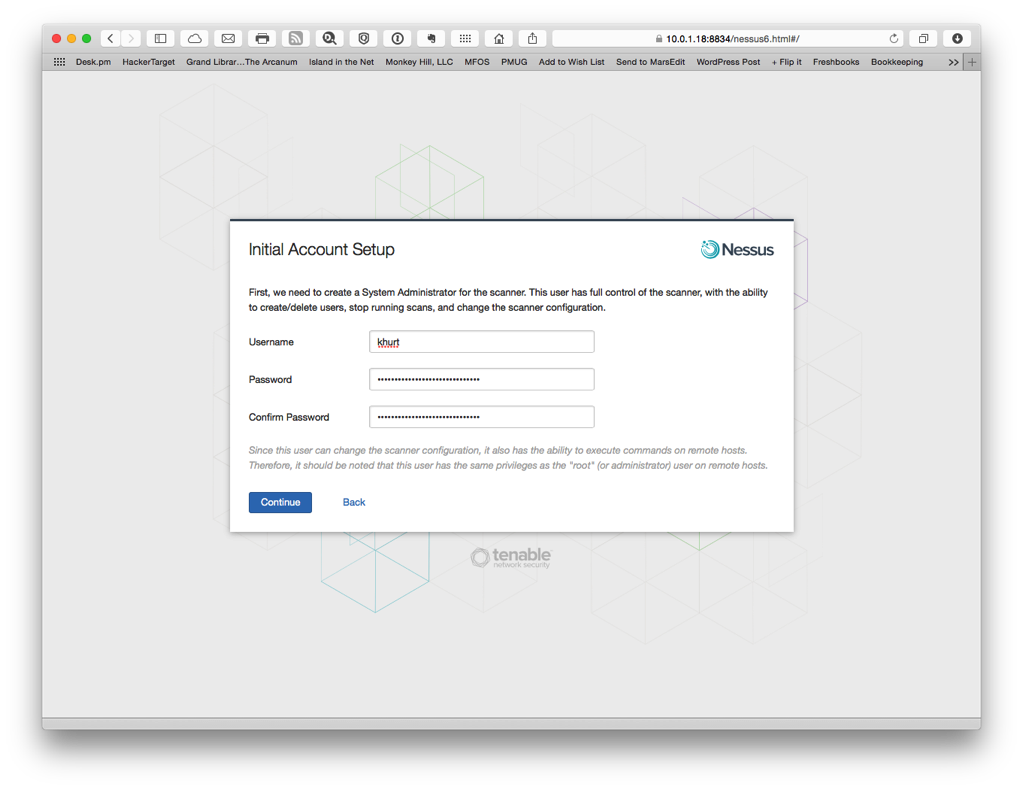
Once setup was complete I started a scan of my network using the default Host Discovery policy. This will allow me to find information about the hosts on my network. I already had a list of hosts so I did not scan the whole network. However, I think it might be useful to know if any unauthorized hosts connect to my network. I have a WPA2 wireless network with a very long randomly generated complex password so it's not likely. Three of my devices are connected to my network via an Ethernet switch. I configured a discovery scan to run once a week and email me the results.
I also scheduled a once monthly vulnerability scan.
I am happy to have a vulnerability scanner working. OpenVAS is the open source version of Nessus but I had some issues getting a working setup. If I can muster the patience I will revisit it. I am sure there is either a web front-end or terminal only client for OpenVAS. I just haven't found it yet. The one downside to using Nessus Home is that my scans are limited to my non-routable addresses. I can scan my home network but if I want to scan my hosts at Digital Ocean I will have to pay Tenable.
NOTE:
Shortly after writing this, I discovered that there is in fact an OpenVAS command line utility. So ... I will revisit using OpenVAS at a later time.